Challenge name
Come Play with me
Category
Malware Reverse Engineering
Level
Hard
Points
200
Description
This strange game can give you the flag, will you play ?
Solution
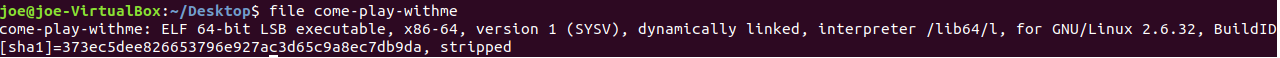
As we can see we are given x64 elf file ,so let’s run the executable and see what it does.
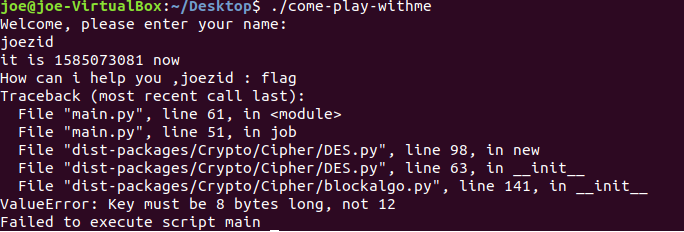
As we can see there is an error due to wrong key legnth ,so it’s clear now that we are working with a frozen python executable. Our goal now is to retrive the source code of the executable first thing we have to do is installing the pyinstaller library.
pip3 install pyinstallerWe will use pyi-archive_viewer command to view the archivefiles in the executable.
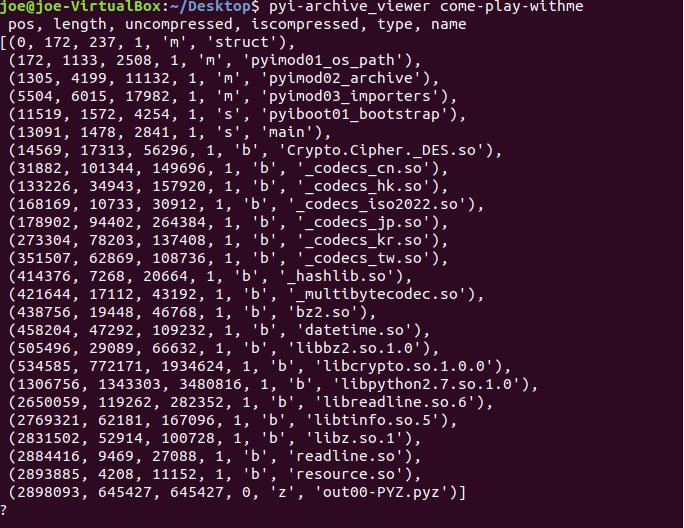
Let’s exract the compiled main.py.
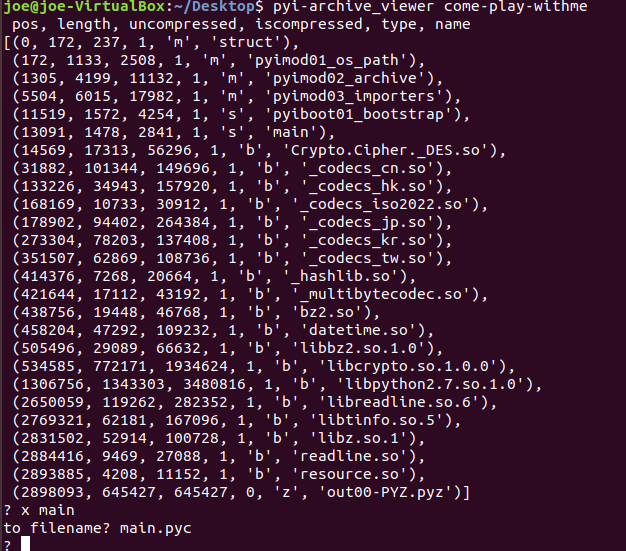
Now we have the compiled version of the main.py so we have to decompile it retrive the source code. We will use uncompyle6 to decompile the main and can be easily install using.
pip3 install uncompyle6Let’s decompile the main.
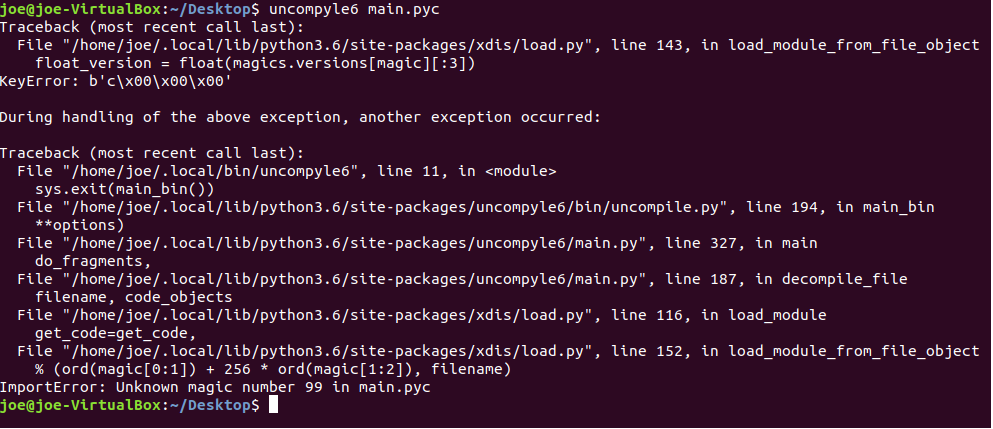
As we can see we got an error due to invalid magic number,To fix this error we will add 8 bytes to the header of the file the first 4 bytes is the magic number for the python 2.7 version and 4 bytes for time stamp (we can set it as zero). Note we have to add these bytes in the little endian format.
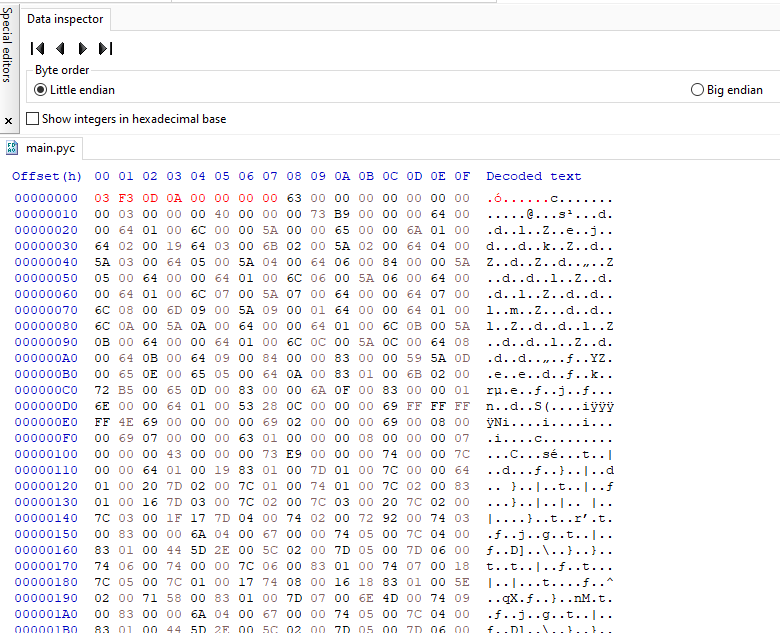
So let’s save the file and try again.
Now Let’s reverse the source code to see how to find the flag.
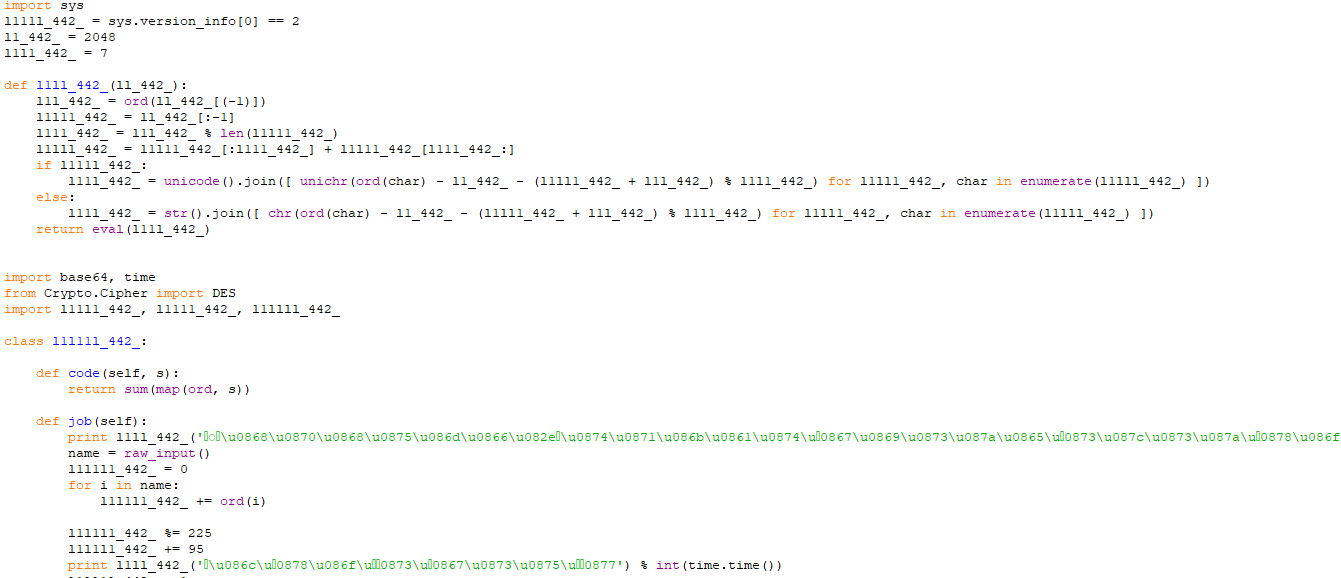
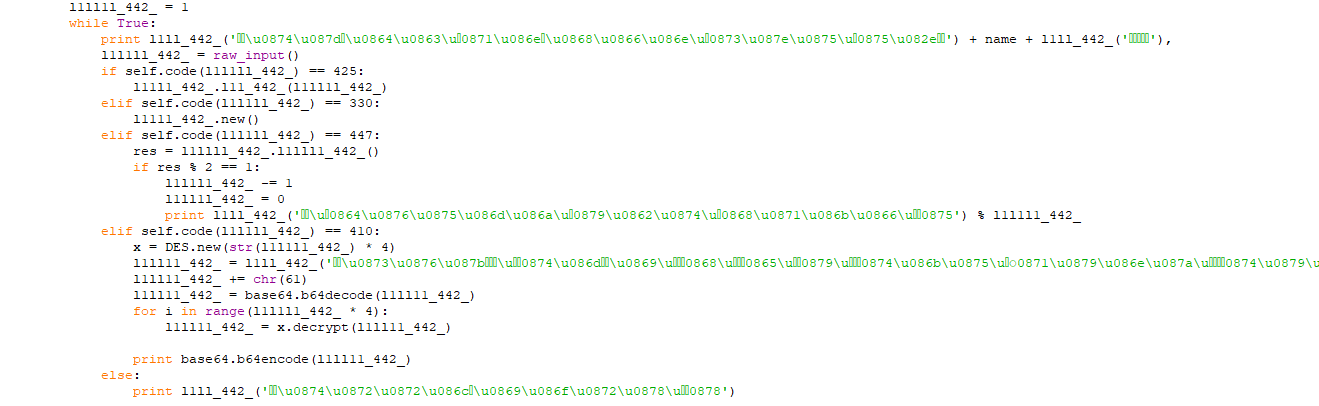
Let’s understand what does this script do, as we can see there is a decoding function whiche decode these this weird looking strings firstly it asks the user to enter his name the calculate the sum of the chars then taking the mod of 225 and then add 95 and this number will be used as the key for the decryption. As we can see at the end of the script the flag is encrypted multiple time so we have to bruteforce the valid key,but first we have to decode the encrypted flag.
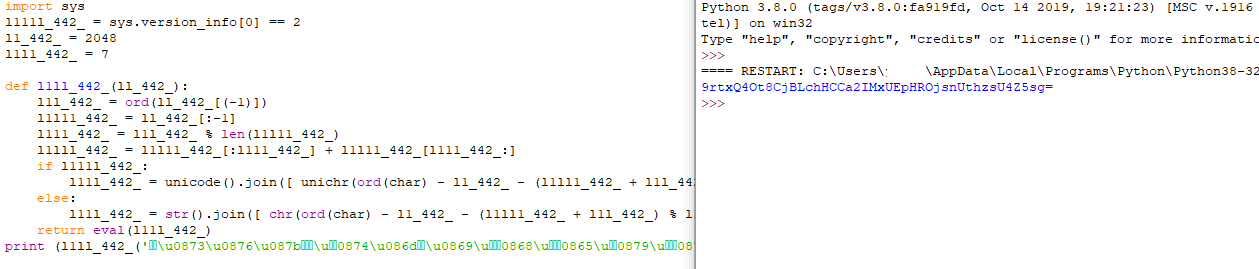
Now we have the base64 of the encrypted flag let’s make a small script to brute force the key.
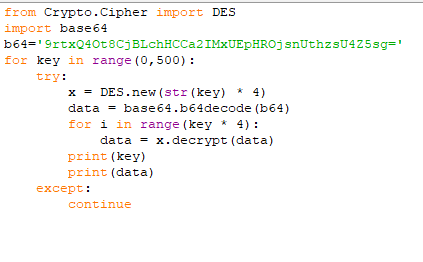
runing the script we find our flag.
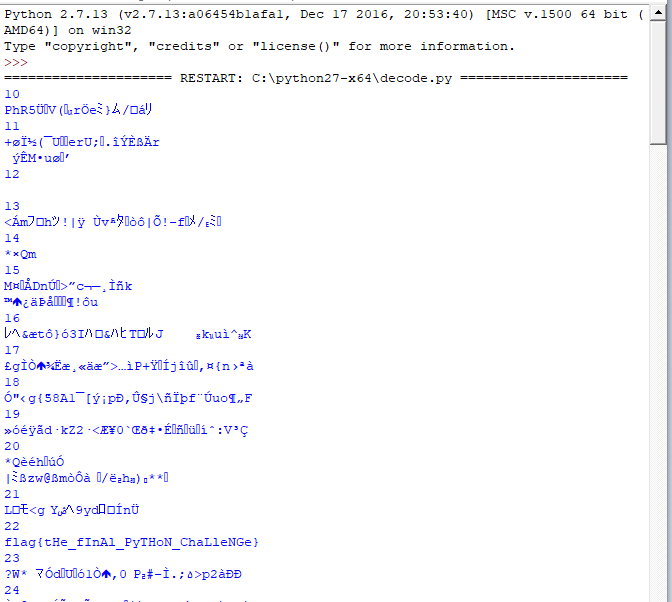
Flag
flag{tHe_fInAl_PyTHoN_ChaLleNGe}
